The Buzz on Cyber Security Company
Wiki Article
Chicago Security Guards & Cyber Security Service";var b="+17734454300";var c="";var d="7545 S Western Ave, Chicago, IL 60620, United States";var e="";var f="";var arr=[];arr.push(decodeURIComponent("%3Cdiv%3E%3Cdiv%20style%3D%22padding%3A%208px%3B%20border%3A%202px%20solid%20grey%3B%22%3E%3Ch3%20style%3D%22margin-top%3A%204px%3Bmargin-bottom%3A0px%22%3E"));arr.push(a);arr.push(decodeURIComponent("%3C%2Fh3%3E"));arr.push(decodeURIComponent("%3Cbr%3EAddress%3A%20"));arr.push(d);arr.push(decodeURIComponent("%3Cbr%3EPhone%3A%20%3Ca%20href%3D%22tel%3A"));arr.push(b);arr.push(decodeURIComponent("%22%3E"));arr.push(b);arr.push(decodeURIComponent("%3C%2Fa%3E"));arr.push(decodeURIComponent("%3Cbr%3E%20%3C%2Fdiv%3E"));document.querySelector('#_nap_').innerHTML = arr.join('');
A cyberpunk then can input malware in their system by using your name. In the following years, more individuals will undergo cybercrimes, these include all individuals: Who have a mobile phone, That have their savings account, That store essential documents and also information on their computers, Whose name is in the direct advertising database of the firms With cybercrimes raising at a disconcerting price everyday, individuals need to take sufficient steps to shield their information or any kind of essential information they may have.
The information can land in have a peek here the wrong hands as well as can become a hazard to the country. So with the increase in the variety of cyber-attacks, the companies, particularly the ones that take care of delicate Click This Link information have to take additional actions to secure the details and also stop the breaching of the info.
7 Simple Techniques For Cyber Security Company
By doing this, when you get he has a good point SSL certificate, which can be of great assistance as it safeguards the data in between the server as well as the web browser. Authentication as well as dependability are two structures on which SSL certificates stand on. To guarantee cyber protection, one needs to make sure that there is sychronisation in all the components of cyber safety.
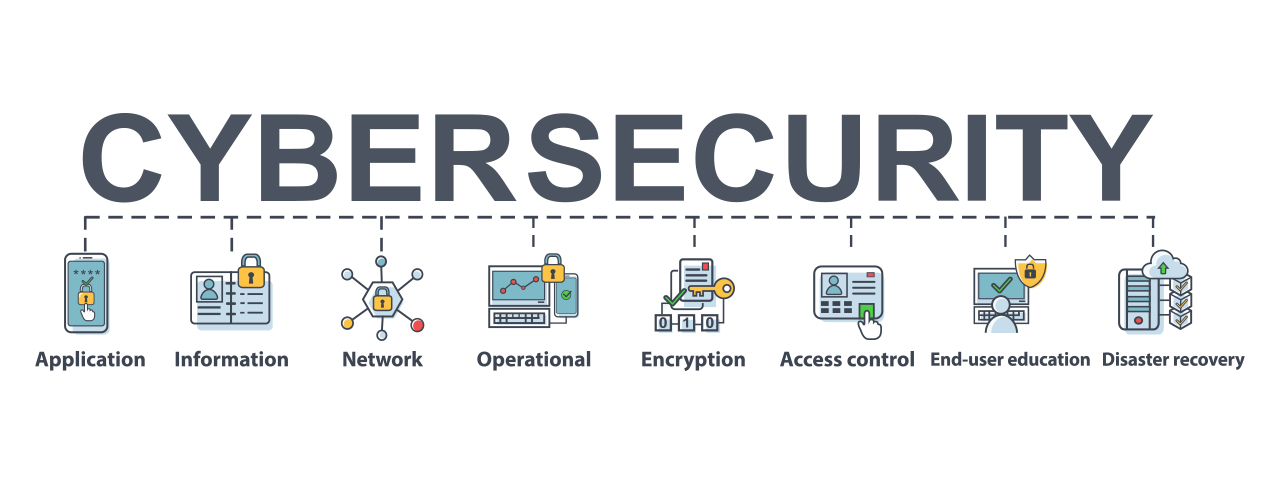
One can enhance the application safety and security by producing protection accounts, recognizing the possible threats, defining the venture assets etc this consists of the advancement of a set of techniques for avoiding, identifying and documenting counter threats to the digital or the non-digital form of details - Cyber Security Company. in network safety and security, one creates the tools that protect the functionality as well as honesty of the network and information.
Report this wiki page